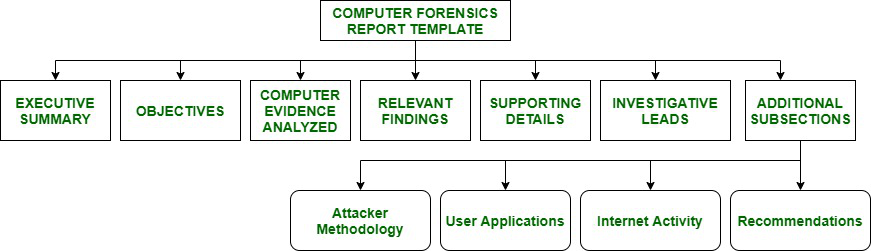
![PDF] Application of intrusion detection system in automatic evidence collection using digital forensics | Semantic Scholar PDF] Application of intrusion detection system in automatic evidence collection using digital forensics | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3c1571b407275e8c1fb446f5a35afe16f006ff70/53-Figure3.1-1.png)
PDF] Application of intrusion detection system in automatic evidence collection using digital forensics | Semantic Scholar

Computer and Intrusion Forensics: Mohay, George, Anderson, Alison, Collie, Byron, De Vel, Olivier, Mckemmish, Rodney D.: 9781630812133: Amazon.com: Books
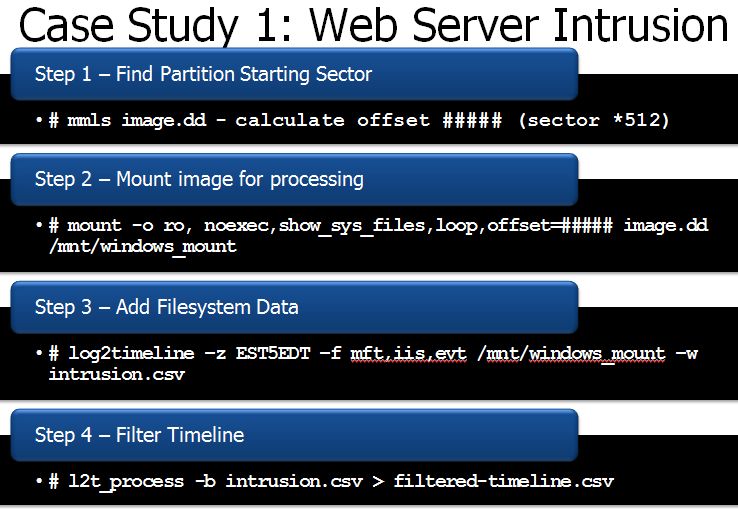
SANS Digital Forensics and Incident Response Blog | Digital Forensic SIFTing: SUPER Timeline Creation using log2timeline | SANS Institute
CFRS 663/TCOM 663 – Operations of Intrusion Detection for Forensics Department of Electrical and Computer Engineering George M